Dynamic, Static and Hybrid Analysis
Using LLVM compiler infrastructure developed dynamic and static analysis tools to uncover insidious bugs, prevent security vulnerabilities, and automate testing and debugging.
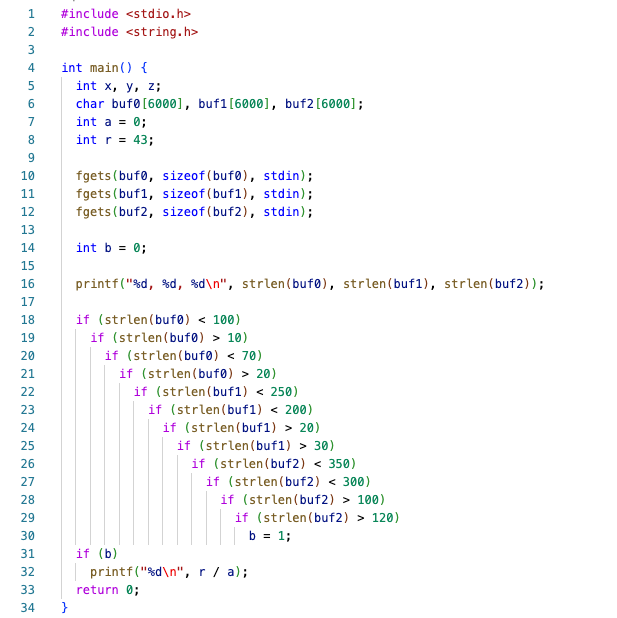
1) Dynamic analysis tool: coverage-guided random input generator - fuzzer. The programs are fed with a seed input,
and fuzzer generates new inputs by inspecting and mutating outputs of previous rounds of tests. Thanks to this mechanism,
bugs hidden in the deep layers of code are possible to be discovered, like a program shown on the first picture.
Example of mutating strategies used are byte swaps/ replacements/ insertions, extanding/shortening input, insertion of special characters, and more.
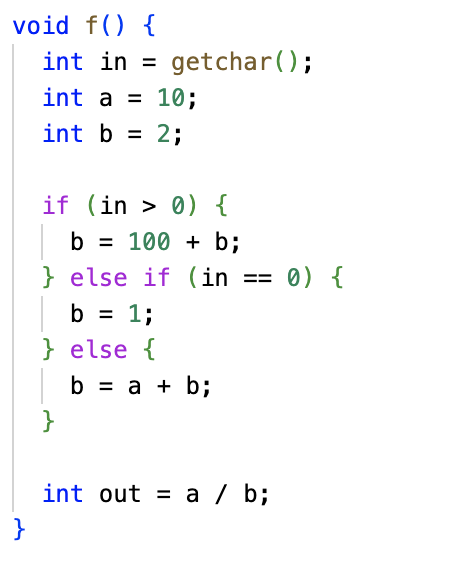
2) Static analysis tools: Delta debugging, constraint-based, pointer and data flow analysis.
They allowed for efficient search for bugs by exploring paths in the code, revealing invariants
and finding a 1-minimal crashing input given a large crashing input. An example output of the Delta Debugger was shown on the second picture.
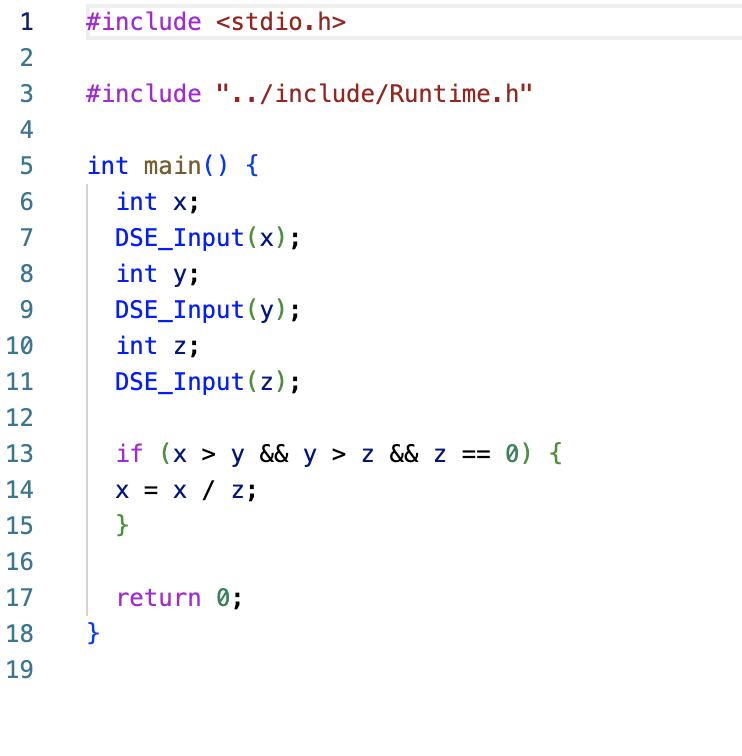
3) Hybrid analysis tool: Dynamic Symbolic Execution (DSE) used techniques from both randomized testing
and symbolic execution. It tracks runtime values and symbolic constraints,
and using backtracking search on program computation trees finds bugs more efficiently than using either of the strategies alone. An example of the program solved by my DSE engine
was shown on the last picture. The engine uses Z3 interpreter, and LLVM instrumentation.